- Login
- Search
- Contact Us
-
Have a question? Our team is here to help guide you on your automation journey.
-
Explore support plans designed to match your business requirements.
-
How can we help you?
-
- AI
AI Without the Hype From pilot to full deployment, our experts partner with you to ensure real, repeatable results. Get Started
- Automation Anywhere AI
-
- Solutions
Featured Agentic Solutions
Accounts Payable Invoice automation—No setup. No code. Just results. Accounts Payable
Customer Onboarding Scale KYC/AML workflows. Customer Onboarding
Customer Support Keep queues moving, even at peak load. Customer Support
Healthcare RCM Revenue cycle management that runs itself. Healthcare RCM
- Products
Platform Features
- Agentic process automation (APA)
- Robotic Process Automation (RPA)
- View all Products
-
- Resources
Get Community Edition: Start automating instantly with FREE access to full-featured automation with Cloud Community Edition.
Featured
 Named a 2025 Gartner® Magic Quadrant™ Leader for RPA.Recognized as a Leader for the Seventh Year in a Row Download report Download report
Named a 2025 Gartner® Magic Quadrant™ Leader for RPA.Recognized as a Leader for the Seventh Year in a Row Download report Download report- Become an Expert
- Developer Tools
- Get Support
- View all resources
-
- Partners
Find an Automation Anywhere Partner Explore our global network of trusted partners to support your Automation journey Find a Partner Find a Partner
- Find a Partner
- For Partners
-
Blog
Top 8 Best Practices for Secure Bot Deployment
Bot security should be top of mind for everyone involved in automation. The Ponemon Institute, which conducts research on data protection and emerging information technologies, estimates that cybersecurity prevention efforts can save businesses up to $1.4 Million per attack. For bot builders and users, following best practices in bot security minimizes risk while speeding deployment bypassing even the toughest IT requirements.
We’ve compiled eight of the top best practices to ensure you deploy safe and secure bots on the Automation Anywhere Bot Store.
#1 Malware analysis
The first step is to perform a malware analysis so that you can be prepared for any unexpected results. Tools such as Virus Total will scan your software against malicious content using antivirus engines. This step is a requirement to list any bots on the Bot Store, and it’s a good practice to follow in your own organization, as well.
#2 Static and dynamic analysis
As a pre-deployment activity and part of ensuring your bot is free from common security vulnerabilities, such as insecure dependencies or cleartext passwords embedded in code, the application source code should be scanned by a reputable analysis scanner. Some examples of reputable tools include Veracode, Coverity, Fortify, and Checkmarx. This is a requirement for Level 3 of the security verification as part of our Bot Security Program.
#3 Software composition analysis
Developers are increasingly using open-source libraries to meet the demands of accelerated development times; however, they are also becoming the most popular attack vector. Any company implementing an open-source library needs to ensure that it is safe to use and ensure that it is up to date on any known vulnerabilities. Companies can integrate SCA tools such as Black Duck and Veracode to provide the ability to integrate open-source security management throughout a DevOps environment from IDE through to a runtime platform. This will enable developers to take advantage of open-source libraries without increasing risk.
#4 Dependency analysis
Another pre-deployment activity that is good to perform is a dependency analysis on your bot. A dependency analysis will examine all dependencies for known security issues. Black Duck can be used to perform this activity. Learn more about dependency analysis through our Secure Bot Developer learning path on Automation Anywhere University.
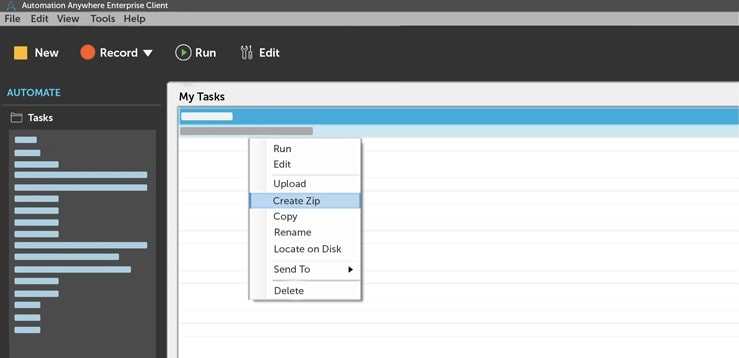
#5 Sideloading necessary bot files
The process of exporting a bot is as simple as right-clicking on it and selecting export to a zip file. To reuse your bot in other automations, or to prepare your bot for Bot Store submission, requires unpacking the zip file and ensuring the bot follows a specific format to enable reusability. It’s a best practice to ensure that any bot includes a README file to document how the bot works and includes the necessary dependencies. If you are publishing to Bot Store, you also need to include the necessary licensing files.
#6 Follow the proper bot deployment format
View the GitHub page that provides a sample bot deployment package and directory structure for all libraries, tasks, and bot resources. Use this as an example when ensuring that your bot package is properly structured and formatted.
#7 Include proper licensing information
Paid Bot Store bots built on Enterprise V11.3.3 (and above) must have a License Info.txt, ATMX Protection Info.txt, and an MBOT Protection Info.txt file in their root directories. Get details on licensing and protection file information.
#8 Include necessary items in README file
Adding as much detail as possible to the README file is important to help bot users understand the security risks and considerations associated with using your bot. The following items are required to meet the security requirements of the Bot Security Program:
- Installation instructions
- Configuration guidelines
- Documentation on all remote connections established
- Use instructions
- All bot functionality and features documentation
- Details of all cryptography use
- List of files/directories/input resources used by the bot
- List of all output locations and output produced
In addition, documentation is required of all errors or exceptions that the bot raises so that any necessary alert/incident management systems can be integrated with it.
Implementing the eight best practices and getting certified through the Automation Anywhere Secure Bot Developer learning path are the most important things you can do to successfully and securely deploy a bot. Applying bot security principles to all areas, from malware scanning to packaging, will help prevent cybersecurity defects with minimal time and energy.
Get More on Bot Security.
About Gautam Roy
Gautam Roy leads the product marketing and strategy of security features for the Automation Anywhere product portfolio.
Subscribe via Email View All Posts LinkedInGet to know the Agentic Process Automation System.

For Students & Developers
Start automating instantly with FREE access to full-featured automation with Cloud Community Edition.